2022年春秋杯网络安全联赛春季赛·Crypto
勇者山峰与传说殿堂都看了题
九点开始守着看的是勇者山峰
当时只有了一道300分的题
notKnapsack
题目
1 | #!/usr/bin/python3 |
对output简单处理了下,然后分析加密代码,可知这是累积的特殊背包问题,搜寻无果,z3不好用。
仔细看题目,说不是背包,或许另有妙计。
时间已过去两个半小时。
十一点半,刷新发现又上了一道500分题
Train
题目
1 | from Crypto.Util.number import* |
简单审计代码,不了解的hash方式。
无所谓,朴素地想着先写py脚本连上靶机互动一下
结果,发了两个字符串flag,直接送给我了flag🤔
回去看代码,发现确实没限定string长度,不好的题目
1 | import socket |
做核酸、洗澡、睡觉等事件干扰,下午三点左右方才又来看题。
想着勇者山峰没什么了,就登陆了传说殿堂
🤔奇妙啊,一样的题,一样的打法
发现绝对厉害的都在传说殿堂,相对厉害的全在勇者山峰
(到比赛结束前,传说殿堂出一道密码就已经是前30了,勇者前90
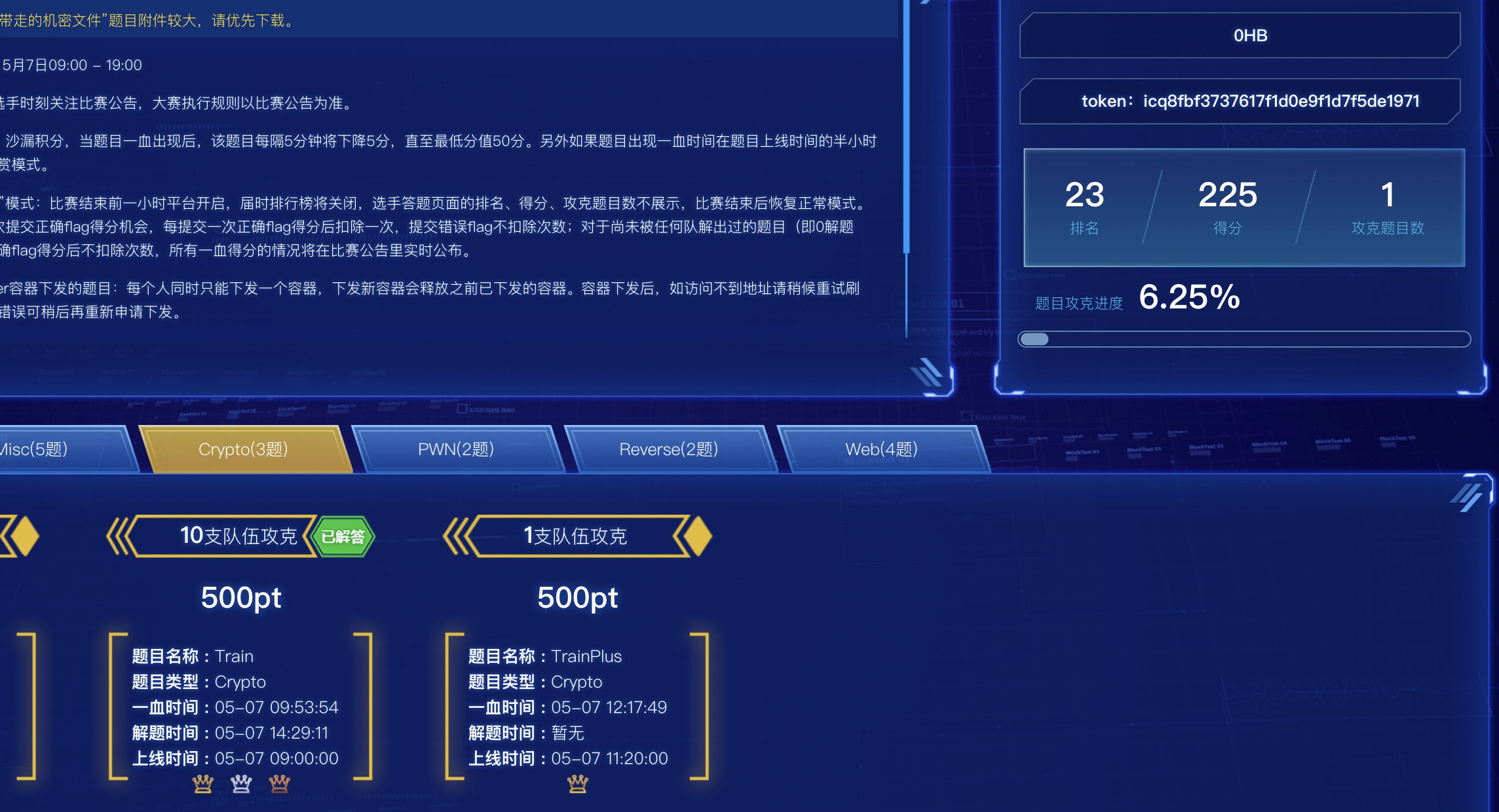
然后就去看了
TrainPlus
1 | from MD_Train import MD00Plus |
1 | def MD00Plus(message: bytes): |
明显感觉到复杂,没什么人出加上自己调试了半天,交互不好,作罢
看回了传说殿堂第一题
bob’s enc
1 | from secret import * |
1 | [[185, 96, 351, 118, 421, 449, 350, 349, 388, 95, 341, 327, 29, 156, 399, 283, 292, 461, 445, 120, 126], [495, 358, 192, 300, 279, 277, 478, 335, 231, 241, 178, 314, 453, 251, 133, 391, 213, 132, 254, 388, 46], [428, 44, 100, 483, 12, 311, 57, 443, 289, 90, 478, 495, 399, 89, 324, 275, 322, 99, 343, 489, 133], [420, 358, 472, 260, 267, 136, 303, 491, 390, 248, 430, 117, 154, 244, 62, 217, 204, 334, 277, 231, 325], [11, 96, 61, 67, 456, 361, 292, 278, 424, 237, 345, 109, 475, 473, 29, 250, 195, 430, 114, 13, 199], [17, 91, 330, 73, 384, 134, 437, 161, 166, 185, 499, 491, 342, 129, 348, 162, 478, 216, 189, 311, 502], [396, 437, 98, 421, 120, 443, 113, 432, 9, 476, 243, 122, 416, 508, 287, 45, 84, 322, 504, 287, 251], [187, 489, 407, 204, 127, 10, 302, 101, 389, 113, 469, 184, 249, 131, 113, 18, 350, 106, 486, 406, 295], [265, 425, 30, 478, 471, 211, 162, 323, 163, 205, 187, 422, 452, 226, 230, 367, 478, 229, 365, 395, 294], [360, 193, 180, 253, 337, 453, 16, 352, 243, 107, 171, 46, 25, 234, 46, 479, 267, 267, 171, 188, 127], [379, 360, 109, 360, 403, 343, 75, 306, 138, 40, 41, 253, 428, 401, 464, 495, 21, 296, 319, 410, 440], [28, 209, 1, 233, 458, 266, 301, 359, 469, 304, 264, 368, 339, 25, 490, 343, 404, 488, 275, 262, 274], [180, 372, 133, 341, 29, 352, 326, 89, 323, 479, 68, 76, 247, 225, 159, 163, 180, 160, 171, 7, 322], [322, 295, 28, 467, 361, 169, 190, 71, 456, 140, 456, 202, 295, 424, 428, 18, 286, 233, 470, 303, 429], [234, 37, 128, 175, 282, 509, 54, 186, 177, 23, 348, 487, 473, 377, 81, 225, 154, 511, 364, 120, 280], [262, 82, 383, 490, 128, 448, 289, 420, 239, 374, 392, 149, 217, 398, 441, 480, 453, 503, 318, 285, 418], [0, 347, 223, 381, 469, 208, 424, 435, 404, 64, 107, 73, 490, 116, 445, 392, 194, 287, 66, 325, 261], [99, 26, 489, 114, 3, 351, 494, 174, 369, 354, 379, 187, 90, 202, 286, 37, 48, 397, 298, 65, 499], [455, 114, 349, 401, 5, 139, 314, 227, 134, 258, 270, 135, 287, 332, 298, 272, 167, 43, 271, 484, 177], [448, 78, 479, 324, 170, 7, 230, 173, 214, 65, 91, 497, 68, 391, 44, 205, 364, 471, 460, 312, 122], [452, 360, 448, 169, 240, 496, 302, 3, 354, 266, 46, 22, 151, 498, 461, 314, 169, 88, 30, 487, 258], [282, 222, 260, 503, 106, 420, 315, 307, 202, 238, 224, 329, 351, 190, 137, 294, 171, 309, 19, 186, 391], [69, 501, 283, 96, 159, 459, 437, 192, 293, 479, 79, 49, 299, 205, 177, 360, 36, 414, 118, 194, 270], [6, 419, 459, 254, 97, 455, 445, 239, 277, 278, 226, 23, 146, 151, 273, 378, 141, 281, 480, 388, 213], [181, 508, 347, 447, 467, 351, 503, 262, 375, 74, 49, 48, 364, 492, 400, 305, 25, 207, 278, 163, 11], [320, 94, 400, 15, 201, 53, 130, 137, 219, 57, 20, 239, 467, 352, 373, 395, 58, 4, 446, 332, 41], [205, 385, 446, 185, 470, 268, 308, 461, 265, 75, 75, 104, 108, 14, 334, 499, 207, 363, 94, 505, 363], [299, 292, 112, 203, 7, 240, 499, 343, 396, 482, 383, 61, 476, 101, 187, 265, 428, 53, 24, 342, 201], [421, 286, 305, 79, 324, 216, 163, 193, 362, 57, 472, 449, 169, 33, 280, 202, 237, 376, 382, 2, 1], [379, 33, 151, 51, 353, 295, 145, 220, 147, 251, 90, 344, 96, 31, 185, 250, 270, 420, 365, 373, 356], [228, 299, 87, 113, 458, 52, 26, 228, 294, 97, 384, 493, 380, 209, 257, 20, 375, 2, 316, 129, 492], [479, 346, 57, 488, 183, 185, 18, 422, 209, 318, 461, 159, 469, 145, 44, 58, 441, 490, 510, 194, 192], [254, 398, 510, 159, 371, 280, 331, 23, 99, 150, 175, 151, 42, 473, 164, 35, 97, 174, 115, 24, 270], [280, 76, 254, 293, 491, 76, 128, 301, 240, 357, 192, 372, 343, 34, 386, 468, 313, 41, 285, 507, 282], [271, 91, 507, 16, 128, 8, 326, 102, 355, 371, 313, 292, 433, 2, 459, 14, 258, 498, 146, 446, 309], [386, 88, 502, 4, 399, 272, 49, 69, 51, 465, 291, 289, 417, 271, 374, 337, 46, 393, 19, 429, 91], [407, 35, 337, 51, 41, 460, 222, 448, 499, 381, 59, 468, 440, 216, 86, 236, 91, 18, 123, 68, 145], [384, 30, 454, 419, 275, 164, 72, 195, 489, 458, 419, 148, 269, 150, 358, 188, 109, 27, 42, 34, 123], [500, 184, 195, 193, 68, 19, 329, 511, 280, 69, 113, 124, 102, 274, 43, 374, 408, 64, 314, 309, 473], [72, 145, 242, 2, 367, 371, 143, 166, 325, 74, 414, 94, 269, 196, 124, 94, 14, 351, 111, 465, 503], [70, 47, 439, 170, 306, 82, 233, 36, 346, 234, 157, 468, 83, 85, 424, 157, 258, 120, 270, 136, 286], [442, 173, 254, 271, 420, 507, 297, 473, 296, 511, 98, 133, 37, 498, 468, 17, 260, 318, 168, 490, 124], [50, 35, 252, 472, 406, 400, 439, 89, 309, 393, 332, 324, 260, 215, 8, 322, 357, 252, 124, 358, 457], [93, 102, 478, 224, 428, 10, 238, 368, 113, 502, 148, 7, 395, 97, 73, 306, 40, 395, 9, 254, 319], [282, 277, 295, 425, 59, 21, 136, 230, 207, 1, 29, 170, 14, 337, 371, 437, 359, 10, 100, 374, 24], [3, 270, 289, 179, 434, 489, 470, 343, 478, 156, 177, 72, 13, 266, 475, 23, 148, 102, 210, 270, 323], [464, 466, 277, 191, 426, 20, 266, 33, 41, 249, 452, 475, 265, 421, 282, 250, 233, 287, 495, 170, 300], [379, 35, 137, 106, 155, 81, 154, 382, 30, 237, 294, 478, 321, 384, 48, 111, 150, 4, 454, 446, 28], [57, 355, 94, 253, 297, 424, 415, 480, 68, 356, 415, 73, 41, 171, 491, 130, 92, 180, 506, 326, 463], [279, 43, 202, 35, 397, 257, 120, 11, 231, 369, 221, 332, 47, 236, 58, 278, 75, 117, 33, 130, 358], [142, 335, 339, 112, 38, 82, 426, 211, 174, 389, 137, 96, 431, 113, 112, 500, 145, 44, 313, 96, 187], [246, 211, 400, 415, 294, 234, 367, 46, 371, 479, 412, 197, 204, 498, 18, 140, 67, 237, 510, 457, 298], [258, 3, 136, 284, 149, 161, 456, 122, 114, 383, 251, 240, 453, 227, 330, 33, 241, 160, 306, 254, 409], [391, 115, 92, 102, 359, 182, 489, 313, 204, 275, 206, 447, 436, 286, 229, 377, 374, 162, 22, 384, 40], [427, 491, 362, 240, 358, 296, 154, 178, 278, 284, 324, 422, 52, 295, 490, 56, 39, 378, 174, 202, 496], [29, 454, 436, 6, 287, 82, 154, 474, 92, 272, 400, 238, 352, 140, 386, 504, 19, 32, 334, 30, 450], [469, 123, 353, 422, 175, 260, 294, 18, 268, 479, 60, 114, 456, 55, 403, 446, 166, 259, 294, 215, 48], [404, 187, 426, 362, 296, 239, 226, 416, 306, 336, 1, 448, 47, 403, 367, 357, 501, 425, 310, 41, 303], [339, 115, 478, 416, 10, 90, 188, 229, 217, 441, 288, 152, 394, 219, 422, 376, 325, 375, 6, 454, 238], [226, 226, 149, 107, 418, 419, 209, 108, 87, 127, 202, 320, 179, 234, 87, 335, 195, 5, 273, 142, 115], [464, 177, 77, 101, 76, 19, 73, 397, 296, 34, 360, 107, 491, 460, 510, 342, 198, 118, 105, 337, 239], [464, 25, 191, 113, 455, 129, 247, 488, 303, 27, 242, 423, 336, 125, 283, 332, 244, 372, 175, 276, 49], [211, 367, 406, 314, 177, 496, 320, 385, 193, 51, 423, 80, 258, 44, 154, 362, 215, 296, 260, 424, 160], [384, 161, 92, 402, 414, 443, 129, 279, 272, 224, 294, 319, 75, 169, 242, 85, 315, 402, 4, 268, 88]] |
la佬一🩸,好奇心拉满,于是开始研究起来了
化简,易得解flag1要点:单模多元线性同余方程
就着csdn现学,效率过低🤔
放弃之际,在github上搜到了优秀的代码
处理好数据,解方程,得到前半段flag
1 | #!/usr/bin/python2 |
困惑于flag2的长度几何,以及噪声的消除方法
这里了解到了LWE
LWE问题
容错学习问题 (LWE问题, Learning With Errors)是一个机器学习领域中的怀疑难解问题,由Oded Regev 在2005年提出,他因此赢得2018年哥德尔奖。这是一个极性学习问题的一般形式。
但很可惜,一小时内没有成功利用之
比赛结束后,回到勇者山峰,发现密码也三道题了
- notKnapsack
- bob’s enc
- TrainPlus
传说殿堂也三道
- bob’s enc
- Train
- TrainPlus
总体而言,难度上,300分的notKnapsack = TrainPlus > bob’s enc >> Train
以及,传说殿堂远远没有勇者山峰卷🤔
后续再跟着其他师傅wp复现吧。
Bob’enc
以下为赛后复现,我决定尽可能多的挖掘此题价值
- 参考尚师傅博客
当时的困惑
- 题目生成列表时,行数列数究竟多少没看懂
- flag2多长
- LWE如何用
现在的未知
- 解题的矩阵思维
- sage命令背后的数学含义
- 过了几个月,学校教的线代已忘
先上师傅总的题解(…Orz
题解
1 | # sage |
flag1
C1 = multi(key, flag1)
对于multi,赛时我的理解是:单模多元线性同余方程
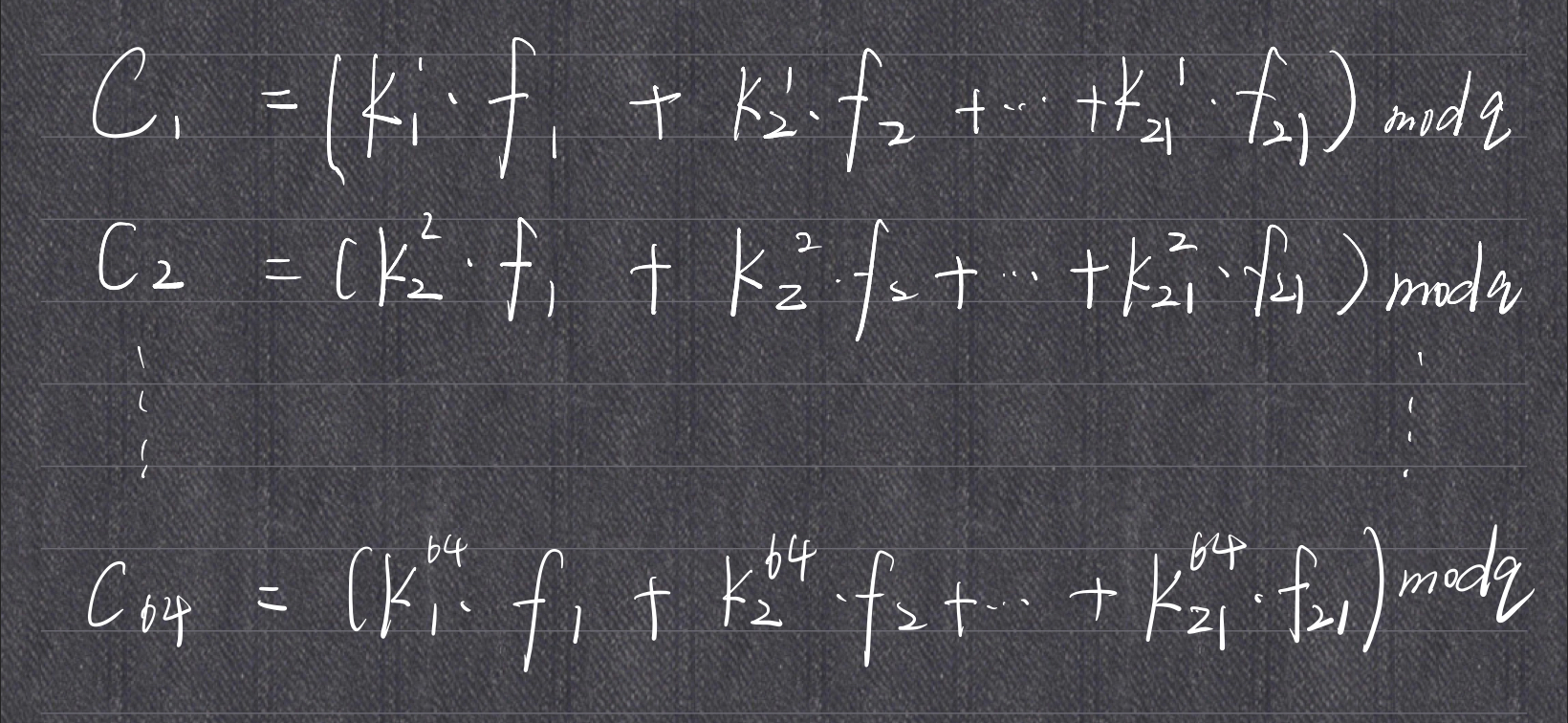
其中out里第一个大列表给了Key(所有ki),第二个列表给了C1(上图左端所有C),所以我找到解此方程的代码,跑出来就是解了。
值得一提,看题目可知,这有64个方程,21个未知量,所以实际跑解方程的代码让C1 = C1[:21]也可
而在高深的密码人看来,C1是由定义在整数域上的p模环矩阵K 乘 向量F [f1, f2, …, f21]得到的:
矩阵K
1 | [185 96 351 118 421 449 350 349 388 95 341 327 29 156 399 283 292 461 445 120 126] |
向量F
1 | [102, 108, 97, 103, 123, 49, 52, 101, 54, 102, 50, 51, 54, 45, 57, 101, 98, 57, 45, 52, 54] |
C1 = K✖️F
1 | (1702, 795, 740, 373, 535, 1308, 1050, 502, 40, 672, 1354, 1843, 515, 231, 774, 65, 978, 1340, 455, 2137, 733) |
经过验证,矩阵与向量相乘为每行对应项相乘再求和,以下
1 | m = |
故不用复杂的求解多个同余方程,可以直接让$K^{-1}*C1$,即可得到:F
- 注意,这里必须左乘$K^{-1}$,即:$C1 = KF; K^{-1}C1 = F$
- 也就是说F是列向量?
1 | from sage.all import * |
整数域上的环,奇妙!
flag2
1 | noise = [random.randint(0,6) for i in range(64)] |
C2 = multi(Key, flag2)
C2 = add(noise, C2)
噪声打断了思绪,得重新整理整理。
赛时也了解到了LWE,但因为不知原理,不懂使用,故无所突破。
按照当时的想法,认为此法能消掉noise就很🐮了,但赛后发现可以直接给到flag2🐮🐮🐮
水平、时间有限,LWE系统的原理学习暂先搁置,先试着读读看使用方法与代码

简单翻译翻译,在此题中,则是给定Key矩阵,先令矩阵Key*向量flag2后再与noise相加,故:
- A = Key
- s = flag2
- e = noise
- b = C2
而LWE问题就是给A、b, 求s
所以一开始所惊叹的‘能直接求出flag2’,在此印证
1 | #脚本2-大规模 |
也发现,我们不需要知道flag2的长度
收获
- 矩阵、向量解题思路
- LWE消除噪音
- 加深对sage的了解