DES算法学习笔记
一般来说,DES算法中
密钥长度为64比特(实际为:56比特 + 8位校验)
DES以64比特为一个单位进行加密,称这64比特的单位为分组。
以分组为单位进行处理的密码算法称为分组密码。
这里学习、记录最为广义的DES(即:具体的操作细则、操作逻辑可以被人为改动
先附上一张完整的大图。
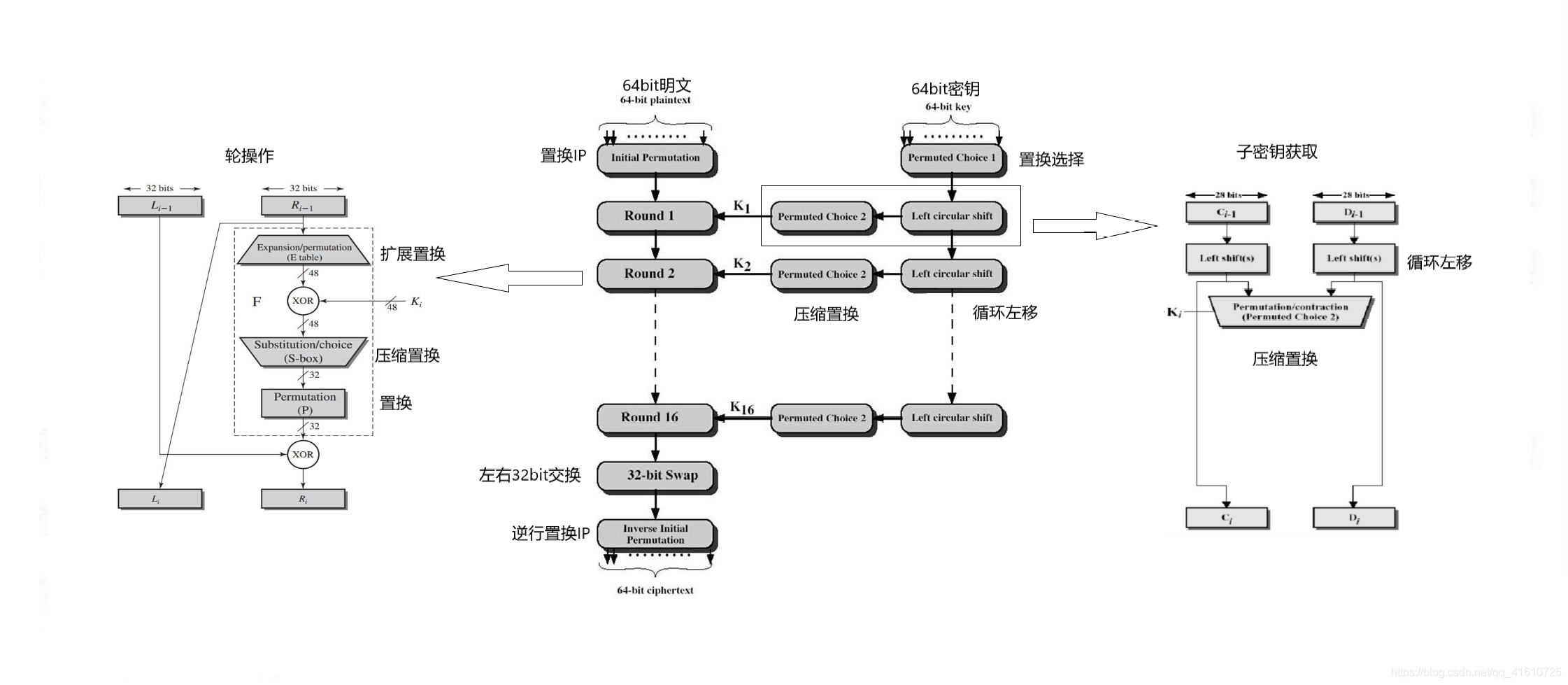
乍一看,难免云里雾里
便从局部入手,慢慢向整体靠拢
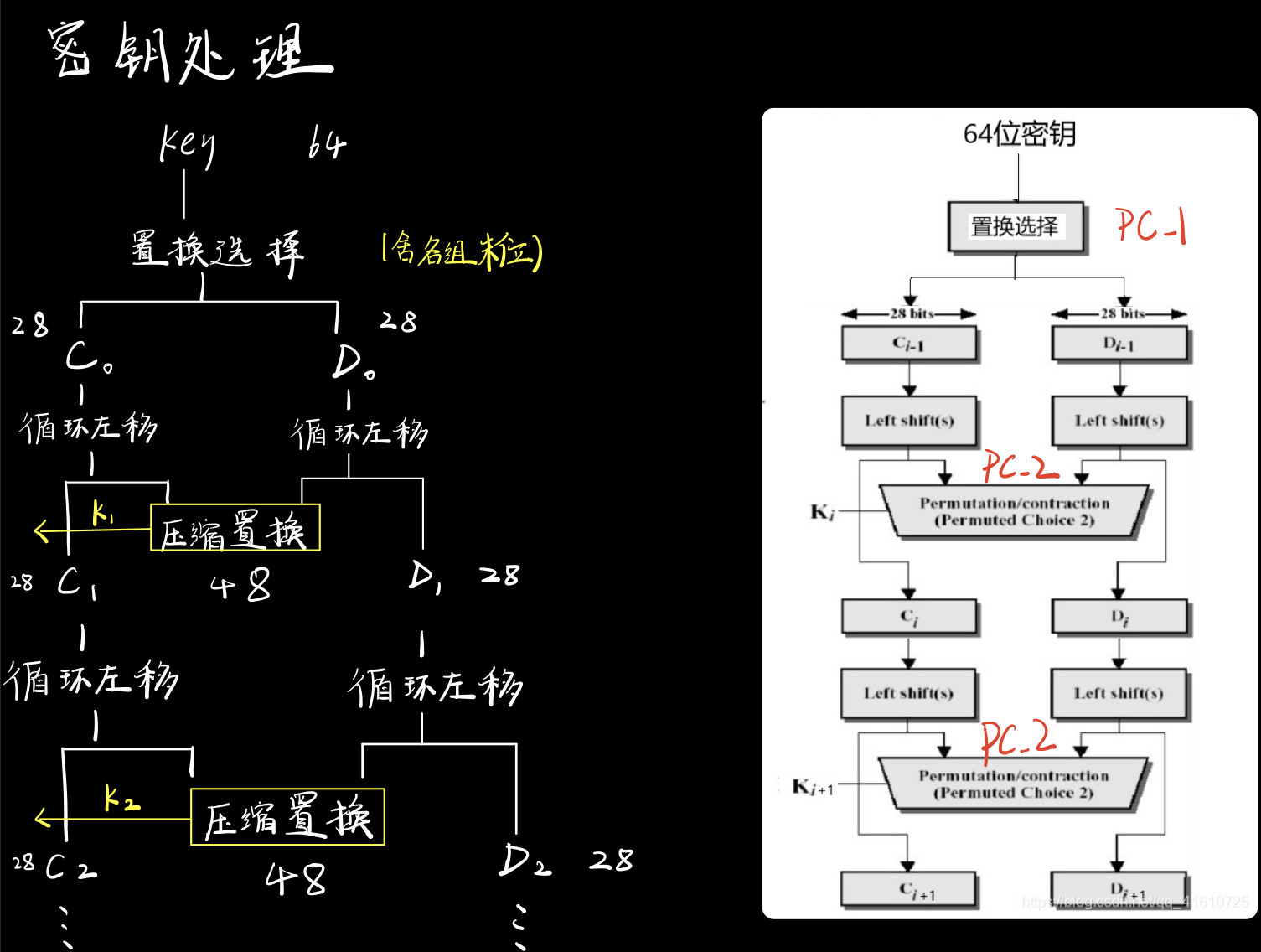
密钥处理
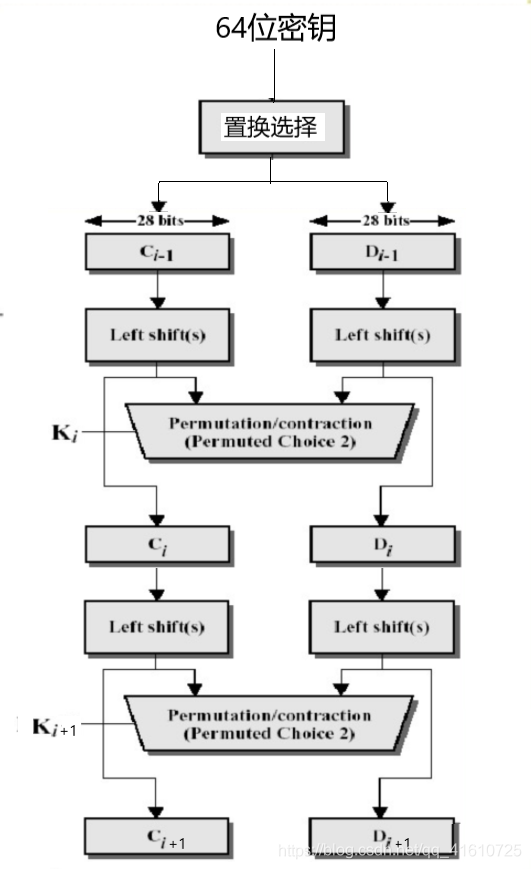
由上往下,慢慢解释。
置换选择 | Permuted Choice 1
(64位密钥,每8位为1组)不考虑每组的第8位,DES的密钥由64位减至56位
每个字节的第8位作为奇偶校验位,这里选择忽略之
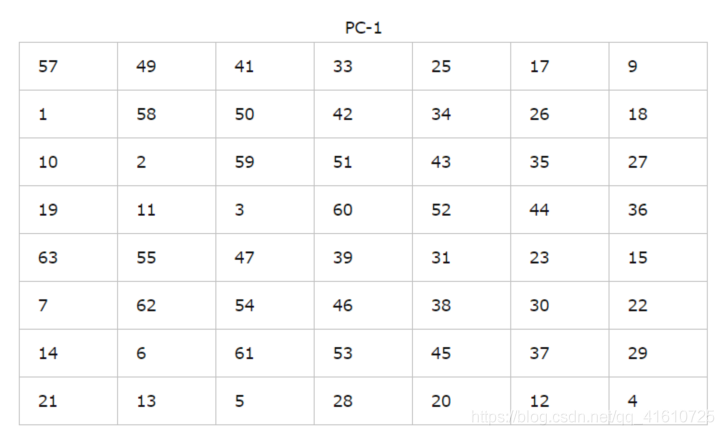
产生的56位密钥由下表生成(表中没有8,16,24,32,40,48,56和64这8位)
生成方式为:
表中第1位57:将原来密钥中第57位 放在 第1位
表中第2位49:将原来密钥中第49位 放在 第2位
······
从上往下,从左往右直到最后一位
置换后的56位密钥分成两部分 C0(28位) 和 D0(28位)
例:
1 | k= 00010011 00110100 01010111 01111001 10011011 10111100 11011111 11110001 |
循环左移 | Left shift
- 将C0和D0进行循环左移变化,变换后生成C1和D1
- C1和D1合并
例:
1 | # 第一步置换后的C0和D0 |
注:每轮循环左移的位数由轮数决定(见下图)

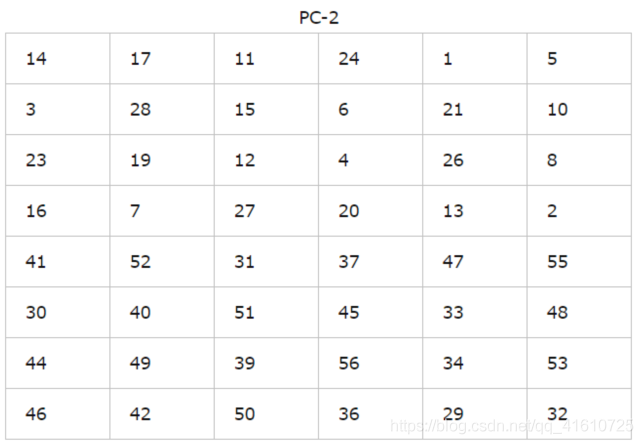
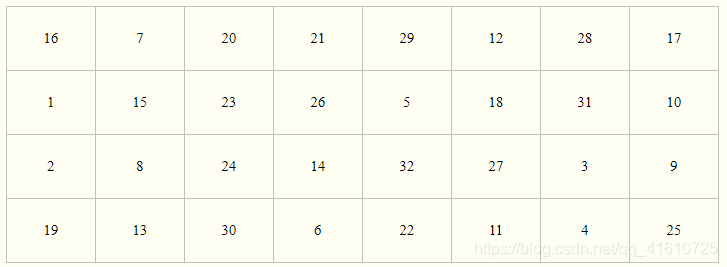
压缩置换 | Permuted Choice 2
移动后,从56位中选出48位。
这个过程中,既置换了每位的顺序,又选择了子密钥,因此称为压缩置换。
换PC-2表规则置换
(注意表中没有9,18,22,25,35,38,43和54这8位)
例:
1 | # 左移后 |
压缩置换后的48位子密钥将参与到轮操作中
而C1、D1也将再进行左移和置换后得到下一轮的子密钥
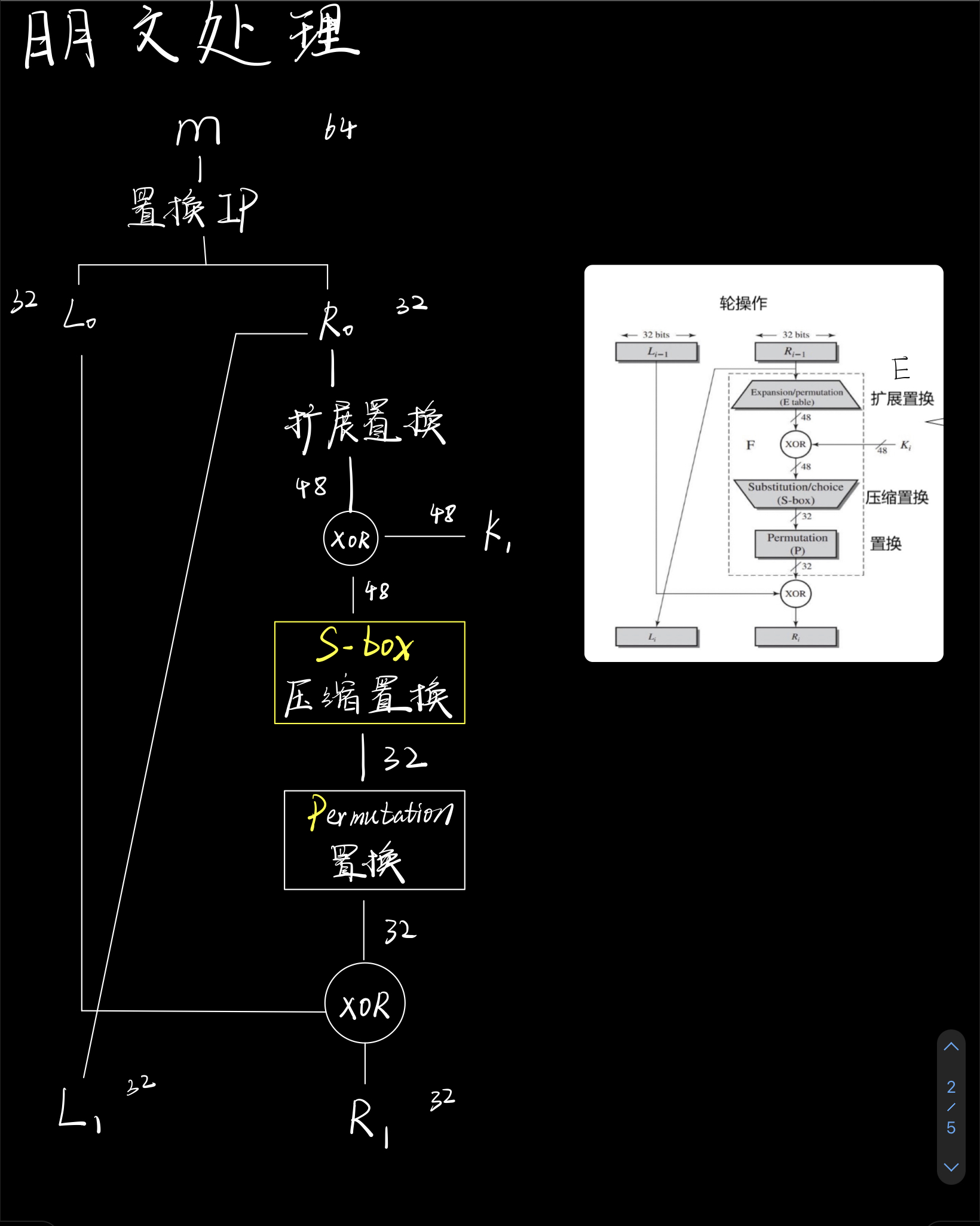
明文处理
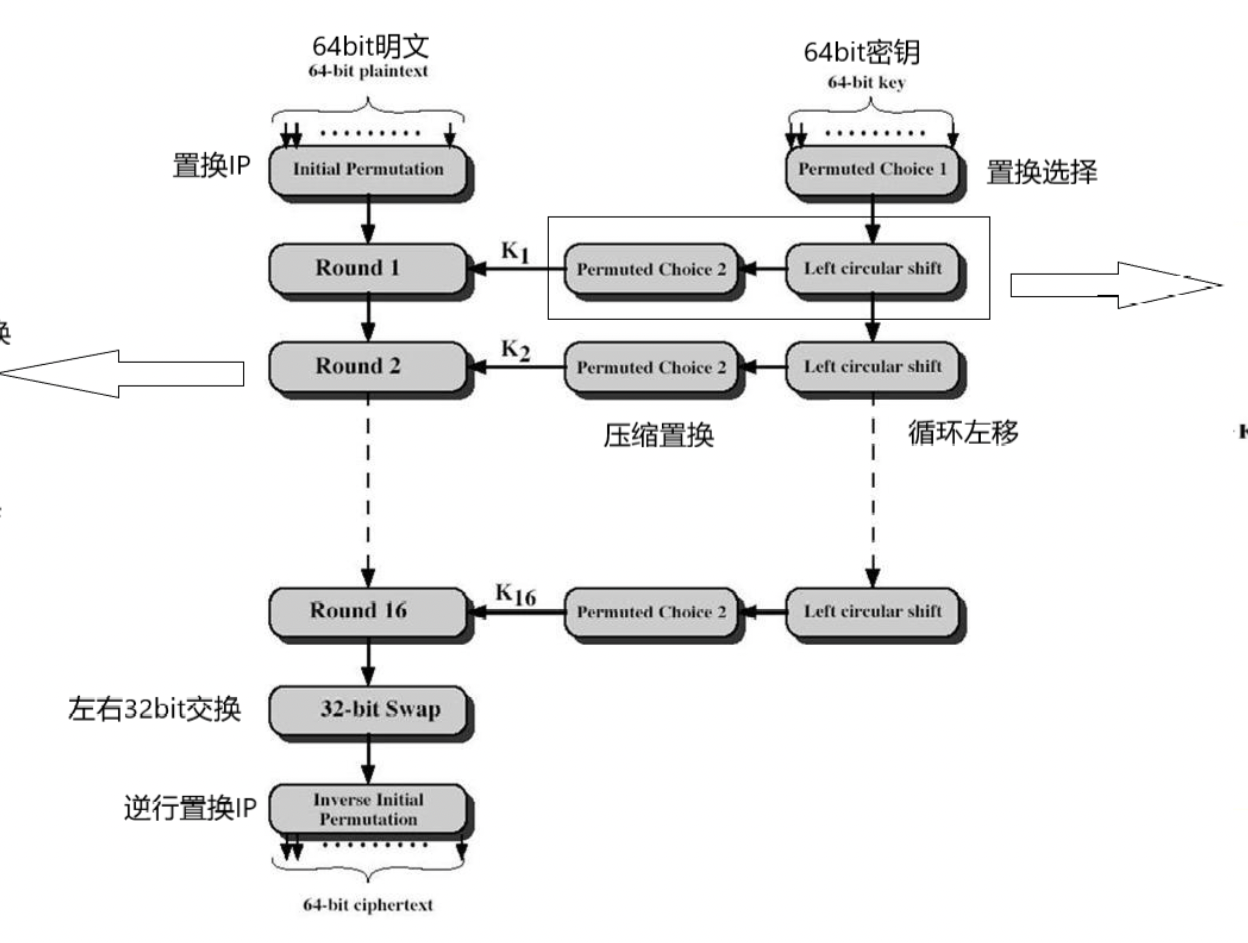
由上往下,慢慢解释。
置换IP | Initial Permutation
64位明文M按如下规则重新组合
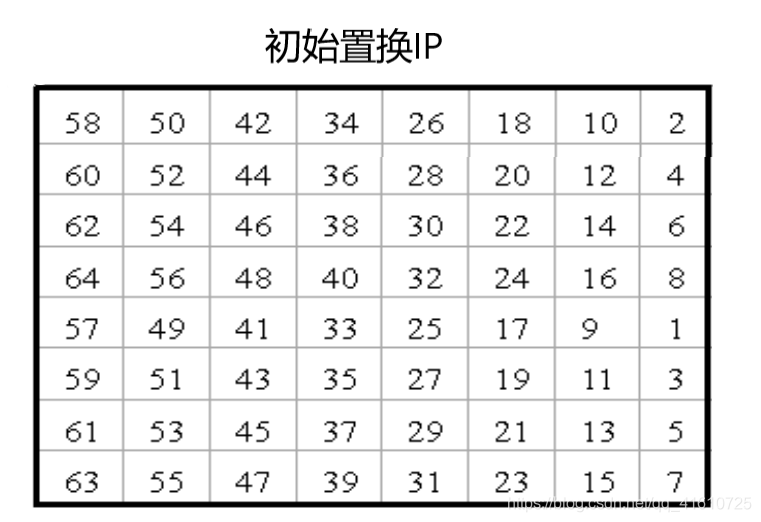
输出分为L0、R0两部分,每部分各长32位
例:
1 | M= 0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 1010 1011 1100 1101 1110 1111 |
轮操作 | F
经过置换IP后的L0、R0会经过16轮的相同操作 (F)
每一轮都会有一个密钥处理过程生成的不同子密钥参与
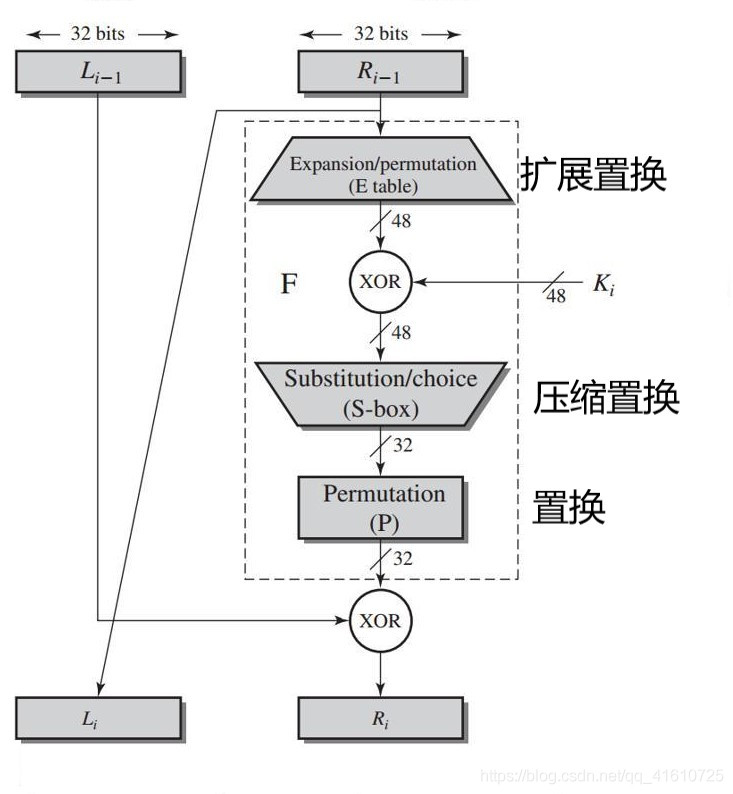
Bring it on.
扩展置换 | E table
扩展置置换目标是IP置换后获得的右半部分R0,将32位输入扩展为48位(分为4位×8组)输出。
按表置换
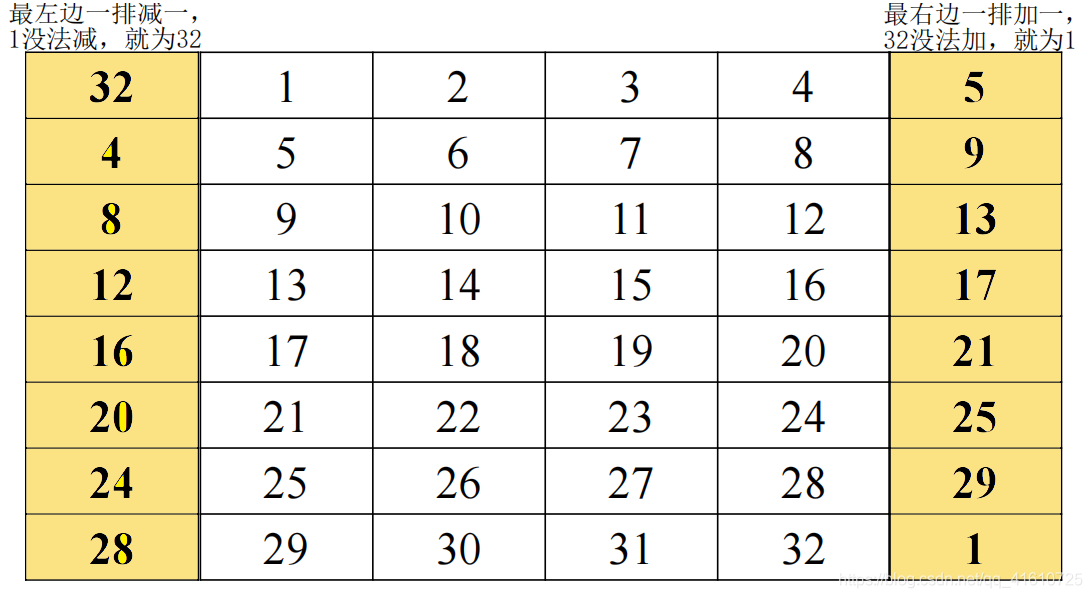
注:左右两边黄色就是用来扩展的
例:
1 | # 明文经过置换后的右半部分如下所示 |
异或 | XOR
- 扩展置换后产生的48位 与 对应的 在密钥处理中产生的48位子密钥异或
S盒置换 | S-box
异或后得到48位的数据,将被送入S盒(6位输入4位输出)进行运算
48位输入分为8个6位的分组,一个分组对应一个S盒,对应的S盒对各组进行代替操作,最后得到32位的数据。
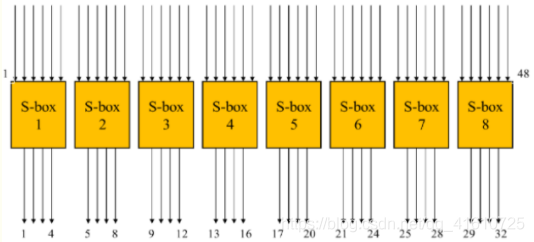
一个S盒就是一个4行16列的表(见下图),盒中的每一项都是一个4位的数。
S盒的6位输入确定了其对应的输出在哪一行哪一列
输入的高低两位做为行数H,中间四位做为列数L,在S-BOX中查找第H行L列对应的数据
例:
- S盒的6位输入为101100
- 取最高位及最低位得到的值10转换为十进制为2
- 除去最高位及最低位的四位数字组成0110转换为十进制为6
- S盒的输出为第2行,第6列所对应的值 2 的二进制 0010
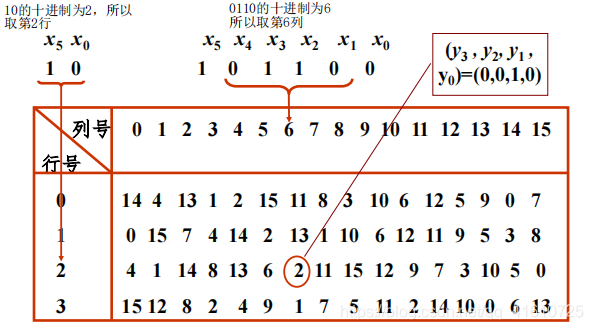
P盒置换 | P
P盒置换即按表置换
特点是该置换把输入的每位映射到输出位,任何一位都不会重复,也不会缺席
例:
1 | # 原数据 |
异或 | XOR
P盒置换的结果 与 最初的64位分组左半部分L0
异或得到结果为 R1, L1则等于R0
接着开始另一轮,总共要进行16次轮操作
左右32bit互换 | 32-bit Swap
进行16次轮操作后,将L16 与 R16互换位置
即
1 | L_ = R16 |
逆置换IP | Inverse Initial Permutation
逆置换是初始置换IP的逆过程(可以好好理解一下这句话
按表置换即可
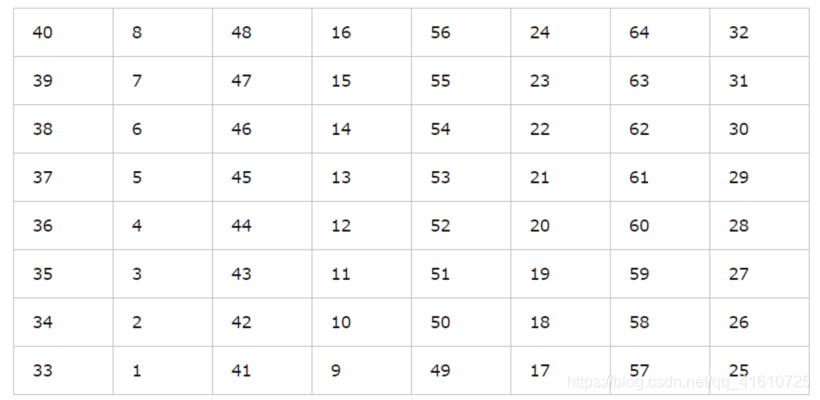
例
1 | L_ R_= 00001010 01001100 11011001 10010101 01000011 01000010 00110010 00110100 |
最后得到的即为密文。
梳理一下
DES会对密钥处理,产生先后16组48位的Ki
DES还对明文处理,使明文与Ki操作,然后产生密文
总体缩略如下
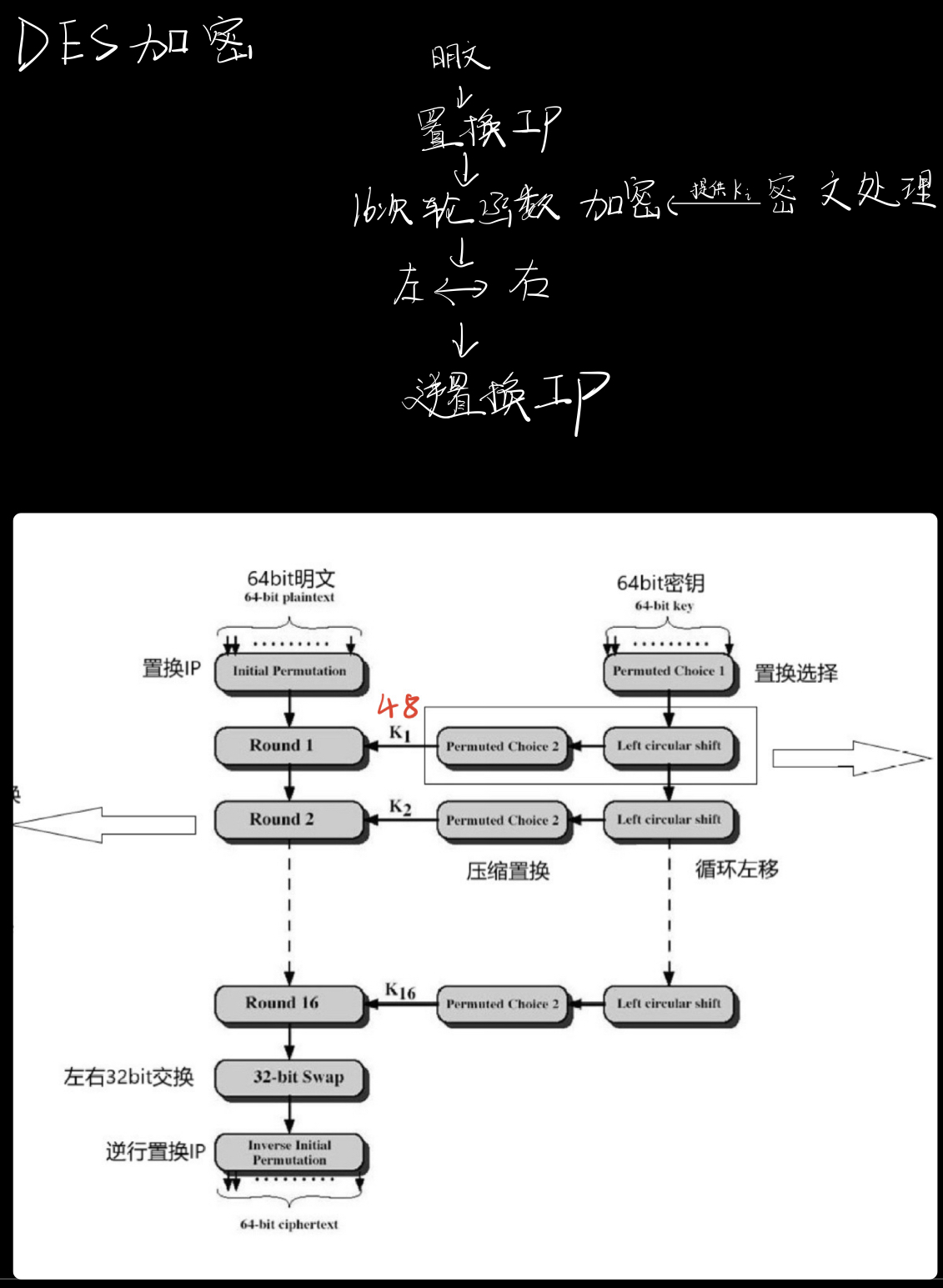
原理讲解的最后,附上最开始的图
应该还算明了,消化一下就好

参考
例题
N1DES
题目
1 | # -*- coding: utf-8 -*- |
题解
给了密钥,密文
依照对称性,写出解密函数
1 | inv_s = [178, 218, 128, 6, 174, 231, 59, 159, 22, 133, 203, 200, 205, 138, 165, 198, 114, 98, 173, 243, 241, 67, 11, 21, 240, 38, 120, 43, 33, 152, 50, 230, 183, 244, 8, 48, 221, 74, 95, 101, 212, 60, 168, 102, 72, 110, 109, 118, 164, 66, 36, 97, 149, 187, 2, 0, 125, 105, 141, 249, 31, 122, 92, 61, 220, 24, 253, 75, 225, 81, 226, 5, 123, 232, 238, 129, 86, 107, 245, 91, 82, 16, 223, 142, 85, 199, 93, 1, 250, 140, 190, 112, 186, 45, 189, 239, 175, 219, 163, 217, 131, 180, 197, 104, 126, 52, 235, 181, 248, 196, 170, 25, 15, 156, 23, 44, 119, 184, 234, 182, 206, 255, 148, 130, 139, 228, 209, 157, 137, 54, 147, 3, 58, 113, 185, 211, 28, 124, 150, 4, 53, 116, 106, 192, 76, 155, 162, 7, 100, 177, 214, 35, 39, 47, 14, 108, 167, 89, 87, 70, 83, 115, 49, 204, 111, 64, 34, 160, 247, 237, 12, 96, 191, 88, 158, 146, 127, 32, 153, 30, 134, 254, 143, 136, 227, 193, 57, 233, 71, 26, 117, 51, 213, 188, 166, 252, 103, 77, 229, 195, 73, 144, 27, 135, 90, 78, 169, 121, 46, 201, 68, 80, 9, 154, 161, 215, 246, 65, 18, 41, 151, 40, 207, 242, 37, 17, 210, 20, 176, 99, 13, 10, 79, 145, 224, 171, 132, 94, 172, 236, 216, 69, 42, 55, 194, 56, 19, 251, 222, 63, 29, 202, 84, 179, 62, 208] |
注意
- 解密时,得用inv_s(S-box的逆置换)
- 解密时,Ki得是反序的
HITCTF2021·baby_des
Hint:Non lined s-box
题目
1 | # -*- coding: utf-8 -*- |
题解
在题目代码下 附加
1 | import os |