2022GoogleCTF·密码复现
前言
复现参考官方仓库
很遗憾,虽然很热血、满怀激情地熬夜打比赛
但被虐的体无完肤,48h队伍0解
「何时才能登陆梦中的彼岸」
ELECTRIC MAYHEM CLS
题目
The server presents power traces of a secret firmware crypto operation. The goal is to recover the secret key. Note, the flag is ‘CTF{XXX}’ where XXX is your recovered key.
题解
学习参考密码魔女的wp
真是糟糕,🧙♀️抄的别的师傅的分析代码(也是日本的师傅)
🧙♀️懂不懂原理我不知,但她确实没讲清楚
涉及“电力解析”,在我看来是很偏的知识点,不具备普适性,暂且搁置
1 | # ref: https://trmr.hatenablog.com/entry/2018/03/18/220441 |
总结
不足
- 搜索能力弱了,接受新鲜事物的能力也差
收获
可以关注关注日韩CTF圈子
不少密码难题的wp都是日韩出的,值得重视
CYCLING
题目
It is well known that any RSA encryption can be undone by just encrypting the ciphertext over and over again. If the RSA modulus has been chosen badly then the number of encryptions necessary to undo an encryption is small. However, if the modulus is well chosen then a cycle attack can take much longer. This property can be used for a timed release of a message. We have confirmed that it takes a whopping 2^1025-3 encryptions to decrypt the flag. Pack out your quantum computer and perform 2^1025-3 encryptions to solve this challenge. Good luck doing this in 48h.
1 | #!/usr/bin/python3 |
题解
只有代码,没有解释原理的wp,看了半小时,看不懂😵💫
先放着吧(中文注释是我尝试理解所翻译的)
1 | import sympy, libnum |
xchgeaxeax师傅分享了他找到的wp,膜拜了下来自日本的密码魔女wp
不得不说,技术力拉满,但魔女🧙♀️表达能力太差了。
也或许是日语机翻的问题,看起来实在太差劲了,一题看一天…
来分析一下题目吧!
It is well known that any RSA encryption can be undone by just encrypting the ciphertext over and over again.
根据题意,“任何RSA加密都能被循环加密所解密”
其后,给了个例子
1 | e = 65537 |
以上为对明文为deedbeef加密的过程
1 | # Decryption via cycling: |
可见,直接对密文加密209次就能得到明文
而根据这个性质,可以人为选好e、n控制好循环次数,达到定时公布消息的功能
之后,给了flag相关的e、n、ct,以及循环次数$2^{1025}-3$
循环次数过于大了,普通机子直接跑48h时间应该是不够的
需要更好的算法求解问题
聚焦循环加密的解密过程,有以下:
$m≡c^{e^{2^{1025}-3}}≡(m^e)^{e^{2^{1025}-3}}≡m^{e^{2^{1025}-2}} \mod n$
可得:
1⃣️$d≡e^{2^{1025}-3}$
2⃣️$ed≡e^{2^{1025}-2}≡1 \mod phi$
对1⃣️,因为d太大了,算不出来,就算我们有了私钥d也不能解出明文,若想着硬算出d同直接循环求解没本质区别
对2⃣️,由欧拉定理,可得:$\phi(phi) = 2^{1025-2}$,记为3⃣️
接下来的手法,我只能从解释的角度出发了,至于当时让我想,应该是想不出来的。
看到官方exp里,有专门的名字,或许是常用攻击方法?还得学习
为解决此题,我们需要找到一个相对够小的d,至少我们能算出来
如何减小d的大小又不影响解密呢?
答案是:$d \mod phi$
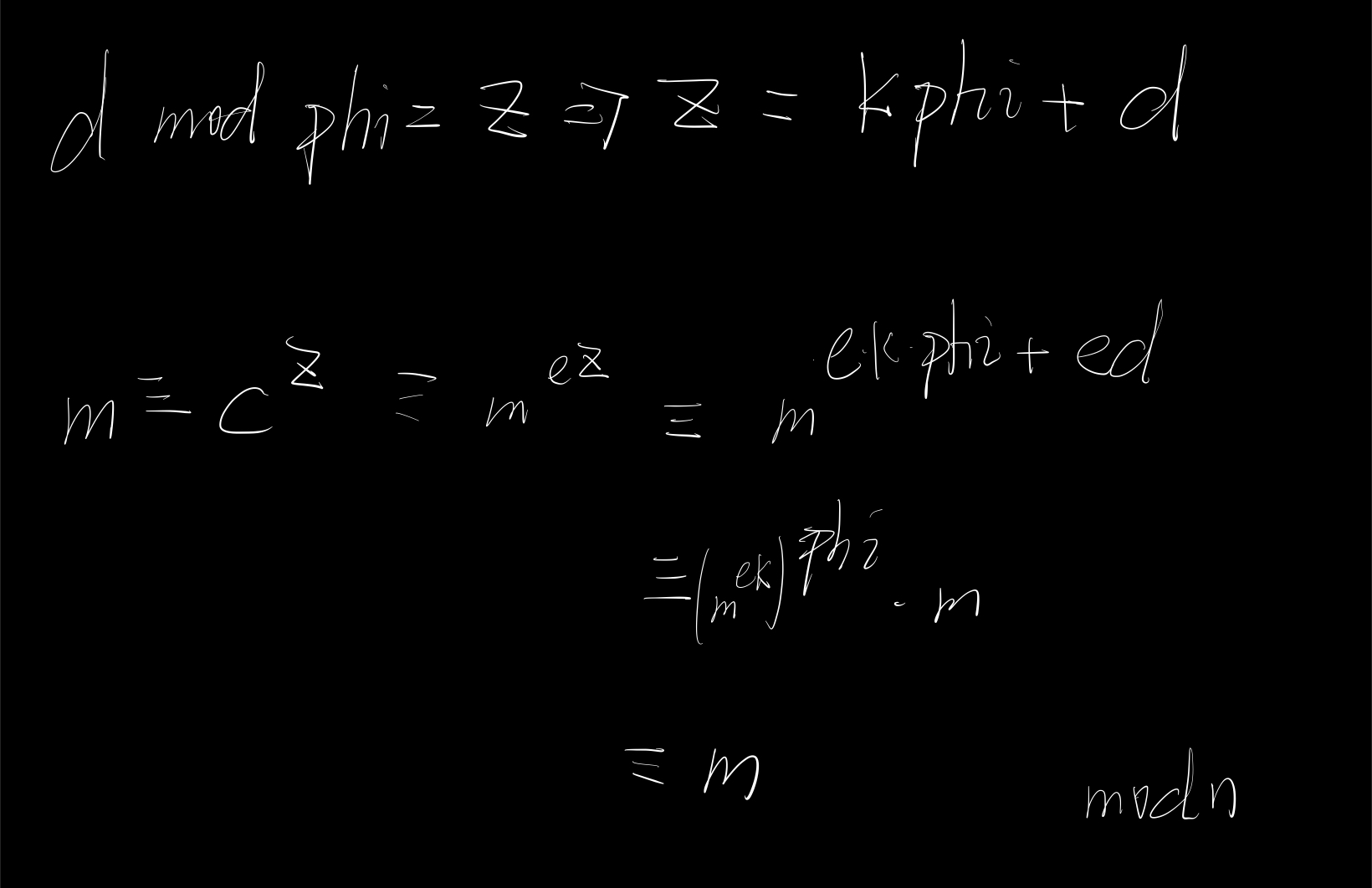
其实,这是走不通的,因为我们不知道phi是多少,这样反而让未知量越来越多了
但,也不是没有收获,针对phi不知的问题,可以利用3⃣️,有:
$\phi(phi) = 2^{1025}-2$
拆之,得:

而设$n=p*q$,则设:$phi=(p-1)•(q-1)=A•B•C•D•E•F•…$
又:$\phi(phi) = 2^{1025}-2=(A-1)•(B-1)•(C-1)•(D-1)•(E-1)•(F-1)•…$
$=a•b•c•d•e•f•g•h•…$
也就是说,$A-1$可能被拆成了$a•b$, $B-1$可能被拆成了$c•e•h$
所以,排列组合并相乘$\phi(phi)$的素因子,再+1,我们能得到含有phi的式子
$(a•b+1)(a•c+1)(a•d+1)···(a•b•c+1)···(c•e•h+1)···$
就会得到$K•A•B•C•D•E•F…=K*phi$
总之,利用$\phi(phi)$的素因子,我们能恢复出$K*phi$
实现代码,如下:
1 | from Crypto.Util.number import * |
再回到如何减小d的大小又不影响解密这个问题,不难发现:
可用$d \mod K*phi$
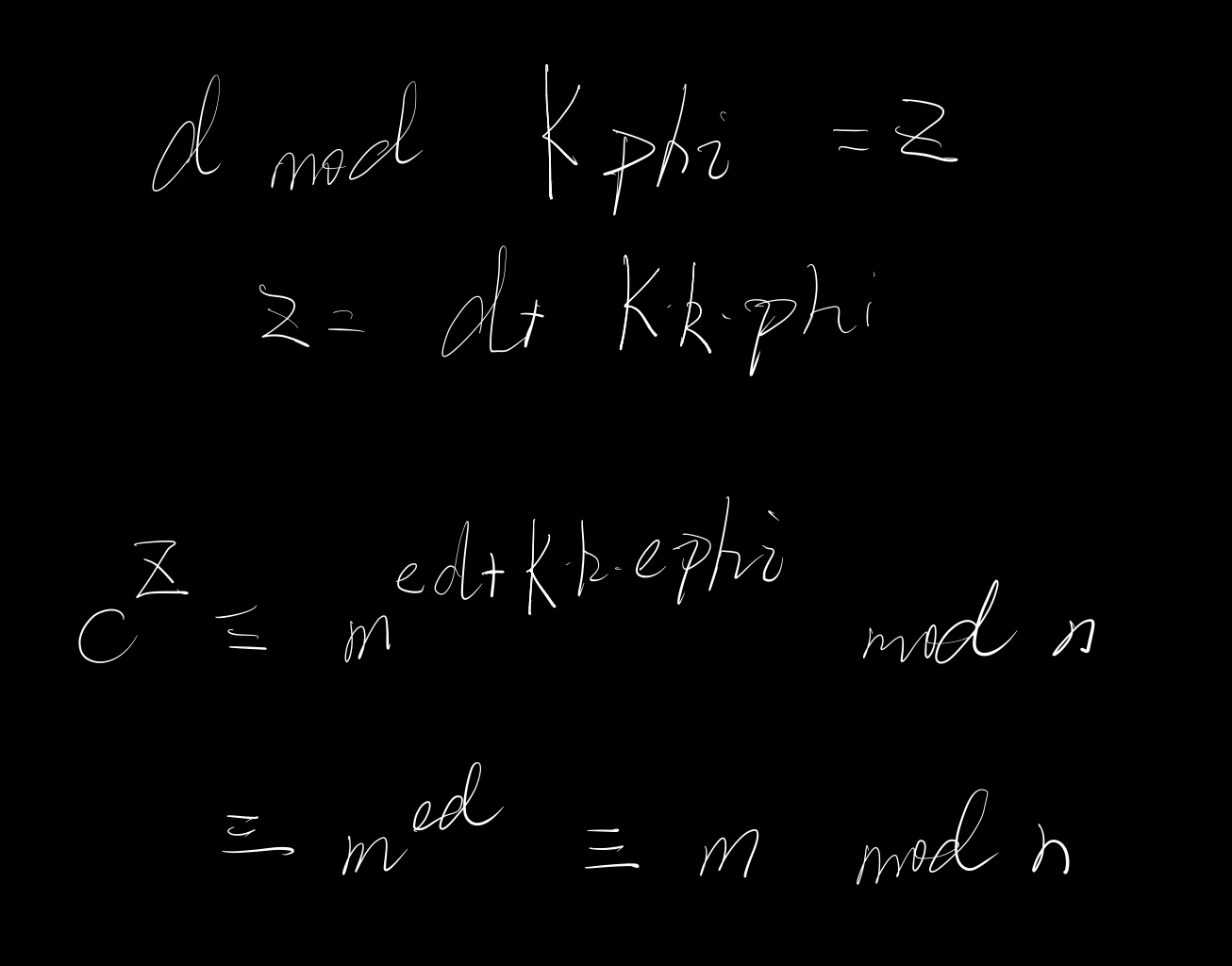
也即:可利用较小的$d \mod K*phi$(原来d为$e^{2^{1025}-3}$)来当私钥d,解密出明文m
(前面算得的K*phi记为res)
1 | p = pow(e,2**1025-3,res) # d mod K*phi |
看到这p = pow(e,2**1025-3,res),会发现这计算量也不小,能不能优化呢?
$e^{2^{1025}-3}≡e^{2^{1025}-2}•e^{-1}≡e^{-1} \mod K•phi$
(哪位师傅来教一下我,为什么可以)
1 | p = pow(e,-1,res) # d mod K*phi |
总代码
1 | from Crypto.Util.number import * |
总结
Cycle attack on RSA
循环攻击给了确定次数,即可攻破
通过$\phi(phi)$获得$K*phi$
d可以放缩成$d \mod K*phi$
MAYBE SOMEDAY
题目
Leave me your ciphertexts. I will talk to you later.
1 | #!/usr/bin/python3 |
题解
学习参考xchgeaxeax师傅找到的日语wp
关于同态的选择密文攻击,时间不够,复现的话,下次一定!
1 | from ptrlib import Socket |